Just for fun and because it’s looking much cooler I wanted to change the canonical domain of 5th.ch to 5th.ch. with the trailing dot of the root domain. So I wrote some .htaccess to do so. After that I noticed my let’s encrypt certificate didn’t match the domain name anymore. 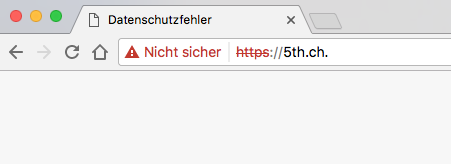
So asked my awesome hoster cyon if I could have my let’s encrypt certificate with the trailing dot.
Doesn’t look like it. =(
@koma5 At this time @letsencrypt hasn't issued any certs with trailing dots (https://t.co/SHfWgZ4hKc%.). 1/2
— cyon.ch (@cyon) January 26, 2017
So I did some digging, hacking and dockering.
Since a domain without trailing dot is ambiguous I was able to trick my browser to load the wrong page.
I setup a DNS suffix on my host machine and the ip of the evil DNS server. This could happen over DHCP in an untrusted network.
cat /etc/resolv.conf
search razw3hgtpmkesdh.com
nameserver 127.0.0.1
The config of the evil DNS server (my first docker experiments):
172.16.42.2 razw3hgtpmkesdh.com
172.16.42.2 razw3hgtpmkesdh.org.razw3hgtpmkesdh.com
If you open the website razw3hgtpmkesdh.org in Google chrome the first query to razw3hgtpmkesdh.org doesn’t get answered. So chrome queries the domain with the DNS suffix appended razw3hgtpmkesdh.org.razw3hgtpmkesdh.com.
You can’t see in the following screenshot that this isn’t the requested site.
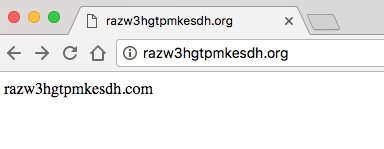
An attacker could easily generate a valid SSL certificate for this bogus site razw3hgtpmkesdh.org.razw3hgtpmkesdh.com. But if the website owner of razw3hgtpmkesdh.com would use the FQDN (razw3hgtpmkesdh.com.) the DNS request would just fail or the attacker could only use a self signed SSL certificate, which wouldn’t be trusted, because he isn’t in control of the real domain.
Using the FQDN as canonical domain isn’t just cooler to look at it’s at least a tiny bit safer.
If you wan’t to try it yourself feel free.